Authentication settings
Authentication settings allow you to define whether an own authentication mechanism with a defined password policy is used or if the system uses a third party authenticator that can be combined with a single sign-on mechanism. (For single users further authentication settings can be configured according to section Authentication and certificates in Parameters of the users.)
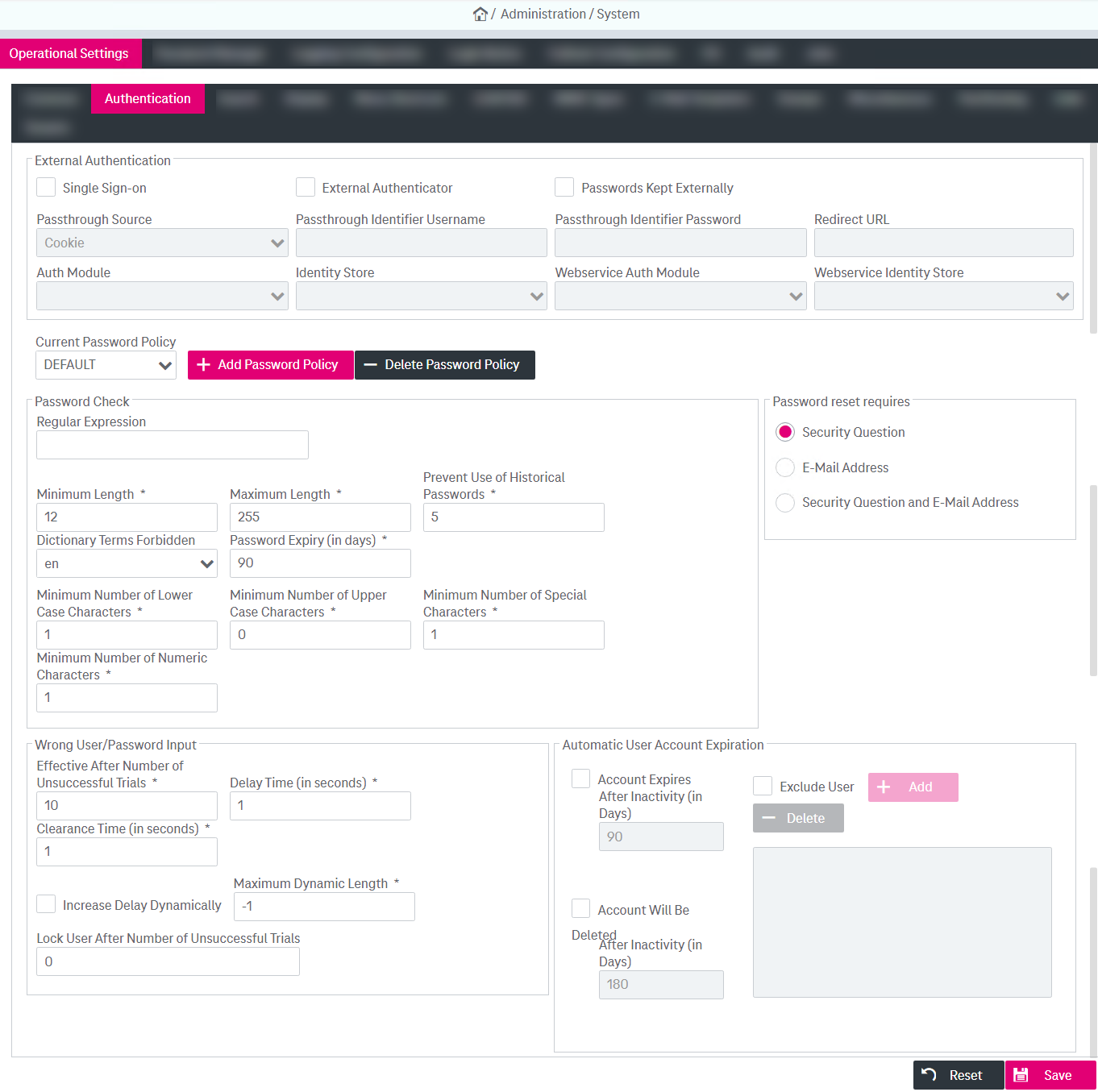
Click the Operational Settings > Authentication tab to configure common operational settings; see figure System – operational settings: authentication below.
The following options are available:
-
to configure external authentication
-
to configure internal authentication
-
to add / delete password policies
To configure external authentication
Use the upper External Authentication panel.
-
Select Passwords Kept Externally.
-
Alternatively, select Single Sign-on (SSO) and define the name of the cookie that is used in order to pass the SSO data. See table Operational settings – authentication parameters for further descriptions. If you select any box on this panel to activate external authentication, all fields on the panels below will be disabled.
In case the SSO setting is enabled, it is possible to access the administration functionality by access to the special login page (login_as.jsf) even if the user is already logged in. Note that the currently running session can be broken in this case after confirmation.
-
ImageMaster offers a set of authentication and authorization methods. To configure the external authenticator, select External Authenticator. See table Operational settings – authentication parameters for more details.
-
Click Save.
You may need to adjust the class name in case of an upgrade:
In practice, a case was observed with an upgrade from 9.7.2 to 9.8.1, where the class name of the external authenticator had to be adjusted:
-
from old: com.tsystems.ima.userlib.ldap.LdapAuthenticationFallback
-
to new: com.tsystems.ima.userlib.ldap.LdapGroupAuthentication
To configure internal authentication
-
Select an entry in Current Password Policy. With sufficient permissions you can also manage this list of password policies; see section To add a password policy below.
-
On the panels below specify the desired rules:
Mandatory fields are marked with an asterisk (*). See table Operational settings – authentication parameters for details.
Internal authentication fields are disabled if at least one box on the upper External Authentication panel is selected.
-
Click Save.
If you have rights to manage passwords, Add Password Policy and Delete Password Policy are visible to you (see figure System – operational settings: authentication). You can define multiple password policies. Only one policy is active and you can change the currently active policy.
-
Click Add Password Policy.
-
Enter the name of the new policy and then click OK.
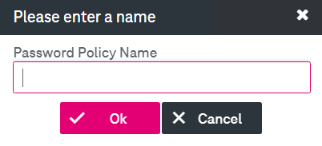
The new policy appears as selected in Current Password Policy.
-
Make sure that the policy to be deleted is selected.
-
Click Delete Password Policy and confirm the deletion in the dialog.
-
Click Save.
Authentication configuration parameters
|
Parameter |
Description |
|---|---|
|
External Authentication |
|
|
Single Sign-on |
Select the box if the authentication should be done by a third party provider. The fields on the External Authentication panel become editable. |
|
Passwords Kept Externally |
Select the box to manage passwords externally (password will not be stored within the system). If selected, the information available in the user’s Profile Settings is restricted to e-mail information, language, date and decimal format settings. |
|
External Authenticator |
Select the box to specify the external authenticator configuration. The following fields become enabled:
For related information see Authentication in [SM IS]. If you use external authentication such as LDAP or RADIUS, further setup of these services is required outside of the AdminClient. For details see the authentication system manual [SM Authentication]. |
|
If the Single Sign-On box is selected: |
|
|
Passthrough Source |
Select the source “Cookie” or “Header”. This field is enabled if Single Sign-On is selected. |
|
Passthrough Identifier Username / Password |
Specify the external User credentials. This field is enabled if Single Sign-On is selected. |
|
Redirect URL |
Optionally enter the redirect URL. This field is enabled if Single Sign-On is selected. |
|
Internal Authentication To enable the fields below, clear Password Kept Externally and Single Sign-on. |
|
|
Current Password Policy |
There is always one default policy. If further policies have been set up, select an entry to switch to another policy. |
|
Add/Delete Password Policy |
Define a new policy or delete the selected one. See sections To add a password policy and To delete a password policy for details. |
|
Password Check |
|
|
Regular Expression |
Enter a regular expression (see chapter Support of regular expressions) to be used as password check for the current policy. If a regular expression is defined, all other policy settings for the password check are ignored and disabled. |
|
Minimum / Maximum Length |
Specify a minimum and maximum length of the password. Maximum Length = “0” means unlimited. |
|
Prevent Use of Historical Passwords |
This value indicates the number of passwords that were last used for at least 60 days which are forbidden. A value of 0 deactivates this check. |
|
Dictionary Terms Forbidden |
Select one of the supported languages. The terms from this language dictionary will be forbidden inside passwords. |
|
Password Expiry (in days) |
Specify the time interval in days which determines the password expiry. The user must provide a new password in the login procedure, if the old password has expired. |
|
Minimum Number of Lower Case / Upper Case / Special / Numeric Characters |
Enter values for the minimum numbers of the corresponding types of characters. The default is “0” for upper case and “1” for the other categories. |
|
Wrong User / Password Input |
|
|
Effective After Number of Unsuccessful Trials Default: 10 |
Enter the number of login failures (with a wrong password) after which a login delay becomes effective. When a delay is effective and a user tries to log in, an error message "Login Delayed" will be displayed. By default (with value 0) the delay mechanism is not active at all. The delay becomes ineffective again, when the time interval specified by “Clearance Time” has passed (see further below). |
|
Delay Time (in seconds) Default: 1 |
Enter the delay time in seconds, which becomes effective depending on the parameter “Effective After Number of Unsuccessful Trials”. If the delay mechanism is active, and a login failed for the first time, the user needs to wait 10 seconds (by default) until a login is possible again. If the option “Increase Delay Dynamically” is activated, which is true by default (see further below), the actual delay time is the value defined here multiplied by the number of unsuccessful trials. |
|
Clearance Time (in seconds) Default: 1 |
Enter the time interval calculated from the last unsuccessful trial after which the delay becomes ineffective again. A value of “0” means that no delay is ever effective because the delay becomes ineffective immediately. Assuming that a delay has become effective and the user waits for more than 60 seconds (in case of the default value) before trying to log in again, no delay is effective anymore. In the server-side configuration, the parameter “loginDelay.attemptTimeout” represents the same option as “Clearance Time” in the AdminClient. |
|
Increase Delay Dynamically Default: false |
Select the box to increase the time of delay after each unsuccessful attempt. If this option is activated, the actual delay time is the value defined by option “Delay Time” multiplied by the number of unsuccessful trials. In the default case this means: after the first login failure the delay is 10 seconds, after the second failure the delay is 20 seconds and so on. |
|
Maximum Dynamic Length |
Maximum amount of seconds for which a login will be delayed when using the dynamic delay increase option. The default value is “-1”, which means that no upper limit is set. |
|
Lock User After Number of Unsuccessful Trials |
Enter the number of unsuccessful login attempts after which the user account is locked. If set to 0 (disabled), the user account will not be locked after repeated failed logins. |
|
Password reset requires |
|
|
Security Question |
Select this option to enable the security question reset mechanism. If a security question has been specified, an e-mail can be sent with a link that directs the user to the security question dialog to reset the password. |
|
E-Mail Address |
Select this option to reset the forgotten password using the confirmation of the used e-mail address without answering the security question. |
|
Security Question and E-Mail Address |
Select this option to enable the security question reset mechanism with the confirmation of the used e-mail address. If a security question has been specified, user has to answer the security question and specify the e-mail address. |
|
Automatic User Account Expiration |
|
|
Account Expires |
Select the box to automatically disable a user account when it is not used for a certain amount of days and enter a number of days in the field After Inactivity (in Days). |
|
Exclude User |
Define a list of usernames that will be excluded from the Automatic User Account Expiration settings. You can add or remove users to / from the list of available users using Add / Delete . |
|
Account Will Be Deleted |
Select the box to automatically delete a user account when it is not used for a certain amount of days and enter a number of days in the field After Inactivity (in Days). |